Posted: No Phising
| Publication year | 2021 |
Posted: No Phising
Lawrence J. Trautman
Mohammed T. Hussein
Emmanuel U. Opara
Mason J. Molesky
Shahedur Rahman
Any engineering approach to cybersecurity must recognize that many breaches are the result of human behavior, rather than sophisticated malware. Effective cybersecurity defenses require a systematic engineering approach that recognizes the organizational, cultural and psychological barriers to effectively dealing with this problem. The U.S. Securities and Exchange Commission (SEC) defines "phishing" as, "the use of fraudulent emails and copy-cat websites to trick you into revealing valuable personal information—such as account numbers for banking, securities, mortgage, or credit accounts, your social security numbers, and the login IDs and passwords you use when accessing online financial service providers." Once this information is fraudulently obtained, it may be used to steal your identity, money, or both.
A review of the literature reveals an alarming lack of attention to the prevalent threat of low-technology, or low-complexity phishing attacks. Accordingly, here is a primer on the prominent exploit known as phishing, illustration of several cases, and the necessity for organizational and societal education of data users as to appropriate computer hygiene. Much of the
[Page 40]
literature about cyberattack addresses technical aspects of computer code, encryption, and bad actor attribution. Yet human behavior remains a significant source responsible for successful cyber intrusions. Your authors believe this Article provides a valuable discussion about the human factors that very often comprise a back-door entryway into data systems.
Overview......................................................................................................41
I. Escalating Global Cyber Threat Environment.......................41
A. Data Breach Costs...................................................................... 46II. Growing Cyber Privacy Risk Factors.........................................48
B. Social Engineering Attack.......................................................... 47
A. Security Breaches, Hacking and Phishing Attacks ..................... 48III. The Phishing Exploit.......................................................................50
B. Growth of Transnational Criminal Actors and Phishing ........... 49
A. What Is Phishing?....................................................................... 50IV. Corporate Responsibility for Corrective Action....................67
B. Spear Phishing ............................................................................ 54
C. Barbarians at the Gate Array ..................................................... 55
D. Romanian Online Organized Crime Ring ................................... 57
E. GozNym Cyber-Criminal Network ............................................. 60
F. Common Indicators of Phishing Attempts .................................. 61
G. Frauds Against Senior Citizens .................................................. 62
H. Protecting Senior Citizens .......................................................... 65
A. Corporate Duties of Loyalty and Care ....................................... 67V. Protecting Yourself from Phishing ............................................71
B. Duty of Loyalty ........................................................................... 67
C. Duty of Care ............................................................................... 68
D. Ormerod-Trautman Cybersecurity Model .................................. 68
A. Recommended Action Steps ........................................................ 71
B. Ease of Usernames and Passwords Access ................................ 72
Conclusion...................................................................................................74
[Page 41]
Any engineering approach to cybersecurity must recognize that many breaches are the result of human behavior rather than sophisticated malware. Effective cybersecurity defenses require a systematic engineering approach that recognizes the organizational, cultural and psychological barriers to effectively dealing with this problem. The U.S. Securities and Exchange Commission (SEC) defines "phishing" as, "the use of fraudulent emails and copy-cat websites to trick you into revealing valuable personal information—such as account numbers for banking, securities, mortgage, or credit accounts, your social security numbers, and the login IDs and passwords you use when accessing online financial service providers."1 Once this information is fraudulently obtained, it may be used to steal your identity, money, or both.2
A review of the literature reveals an alarming lack of attention to the prevalent threat of low-technology, or low-complexity, phishing attacks. Accordingly, here is a primer on the prominent exploit known as phishing, illustration of several cases, and the necessity for organizational and societal education of data users as to appropriate computer hygiene.
This Article proceeds as follows: First, we describe the escalating global cyber threat environment, and examine the high costs of data breaches. Second, we examine privacy issues. Third, we present an overview of the phishing exploit. Fourth, we discuss corporate responsibility for corrective action. Fifth, we provide a few thoughts about defensive tactics available to protect against phishing attacks. And last, we conclude. Much of the literature about cyberattack addresses technical aspects of computer code, encryption, and bad actor attribution. Yet human behavior remains a significant source responsible for successful cyber intrusions. Your authors believe this Article provides a valuable discussion about the human factors that very often comprise a back-door entryway into data systems.
Like their expanding user base, the data collected on Facebook users has also skyrocketed. They have moved on from schools, likes, and relationship status. Today, Facebook has access to dozens of data points, ranging from ads you've clicked on, events you've attended, and your location based on your mobile device.
[Page 42]
It is no secret that Facebook makes money off this data through advertising revenue, although many seem confused by, or altogether unaware, of this fact. Facebook generated $40 billion in revenue in 2017, with about 98 percent coming from advertising across Facebook and Instagram.
—Senator Chuck Grassley Chairman, Senate Judiciary Committee
April 10, 20183
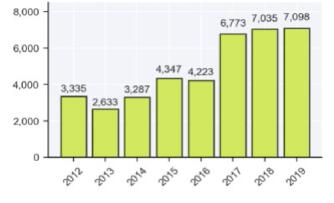
Cyber breaches and theft continue to grow at an alarming rate,4 constituting a threat to business5 and global stability and peace.6 For perspective, during the most recent decade alone, RiskBased Security reports, "there were 986 reported breaches exposing 102,646,498 records in 2010. It only took two years to more than double the number of breaches—2012 jumped up to 3,335 reported breaches—and by 2016 the number of records exposed was consistently over the 5 billion mark."7 RiskBased Security warns, "Looking ahead, we see little indication of improvement. In fact, it's quite the opposite. Low complexity phishing attacks show no sign of slowing, malware is as virulent as ever, and the black market for stolen data continues to thrive."8 Recent key highlights for data breaches are depicted in Exhibit 1.
[Page 43]
• In 2019, there were 7,098 breaches reported, exposing over 15.1 billion records.
• The number of records exposed is [up] 284% compared to 2018, [up] 91% compared to 2017.
• Although the number of breaches in 2019 is only 1% higher compared to 2018, it is anticipated the gap will continue to grow throughout Q1 2020 as more 2019 incidents come to light.
• Web (inadvertent exposure of data online) compromised 13.5 billion records while hacking exposed 1.5 billion records. All other data types combined exposed approximately 120 million records.
• Breaches at technology providers pushed the Information sector to the top spot for number of breaches, followed by the Healthcare sector. . . .10
For additional perspective, RiskBased Security documents, "the number of breaches disclosed in 2019 once again hit an all-time high . . . . [while] the 2019 incident reports were still trickling in [when] this report was created. . . . Looking back at the patterns from the prior three years, we anticipate another 250-300 incidents will be added to 2019."11 Exhibit 2 depicts the number of annual breaches reported.
[Page 44]
Inga Goddijn, Executive Vice President at RiskBased Security, cautions, "as we look over the experience of 2019 what stands out is that we are often our own worst enemy."13 Weak controls and human nature appear responsible for the severity and number of 2019 breaches, "whether it's a phishing campaign that ultimately provides malicious actors with a toehold into systems or misconfigured databases and services that leave millions of sensitive records freely available on the internet . . . ."14 Growing interest in user credentials is observed during 2019 as "Troves of username and password combinations continue to become available on forums and file sharing sites while phishing for access credentials—a perennially popular method for gaining access to systems and services—has surged in recent months, proving . . . social engineering techniques still produce results for attackers."15 RiskBased Security reports:
The breach at Bodybuilding.com is a prime example of this trend. In July [2018], malicious actors gained access to the company's systems thanks to a successful phishing email. Hackers were able to move about the system for approximately eight months, potentially accessing data ranging...
To continue reading
Request your trial
